Accounts and Passwords
Stockton GoPortal Accounts
In order to access Stockton University's online resources (e.g., Go Stockton Portal, Email, Computers, Blackboard, etc.) you need a Go Stockton Portal account. For instructions on how to access the applications and services associated with your Stockton GoPortal account please visit our Cloud Services page for more details.
Password & DUO Mobile Reset Requests
As cybersecurity threats continue to evolve, additional identity verification steps have been implemented to confirm the authenticity of account access requests and protect Stockton University accounts from social engineering attacks. These changes included the following…
- Requests for a password reset or a DUO mobile bypass code now require a valid photo ID for identity verification purposes.
- The self-service password rest tool now requires DUO Multi-factor authentication as an additional layer of account security.
- Account servicing personnel received additional training and tools to help better evaluate incoming requests for their authenticity.
- Internal processes and controls were implemented to assess the authenticity of access requests that don’t meet minimum identity verification requirements.
- Account authentication activity is monitored to proactively address unusual behavior.
Our primary goal is to protect your account and your information from attackers, so while these additional security measures may seem inconvenient, we feel that these changes are the most effective steps to ensure that we are verifying request authenticity. In addition to these changes, Information technology staff continue to monitor new and emerging cyber security threats as part of an ongoing internal training process for our account servicing team so that we can be one step ahead of the next threat.
If you have any questions about our account servicing processes, security practices, or any other general Information Security questions, please don’t hesitate to reach out to us. Our contact information and hours of operation can be found on our website here: https://stockton.edu/information-technology/request-help.html.
Resetting your Portal Password
You can perform a Password Recovery if you forget your password. After resetting your password, don’t forget to update your mobile devices.
DUO Mobile best pratices
Although DUO offers a text message and call option for multi-factor authentic requests, the DUO Mobile application for your smart phone or table is a more secure option. The Duo Mobile app generates time-based passcodes and allows for push notifications, making it both convenient and secure, especially for those that travel frequently. Text and call methods are not as robust due to the potential for interception and may limit your access if you’re traveling internationally or in areas with poor cellular service. Please visit our website for more information about the DUO Mobile application: https://stockton.edu/information-technology/duo.html
Personal Password Protection
Effective password management is crucial to maintaining the security of your accounts. Always ensure that your passwords are complex, containing a mix of upper and lower case letters, numbers, and special characters. Avoid using easily guessable information, such as birthdays or common words, and never write your password down on a sticky note or store it in an unsecured place. Remember, the goal of an effective and secure password is to ensure that it is both complex and easy for you to recall. No one from the Stockton University ITS Help Desk will ever ask you to provide a copy of your password over the phone or via email. If you receive a solicitation for your account credentials, please contact the office of Information security at information.securtity@stockton.edu
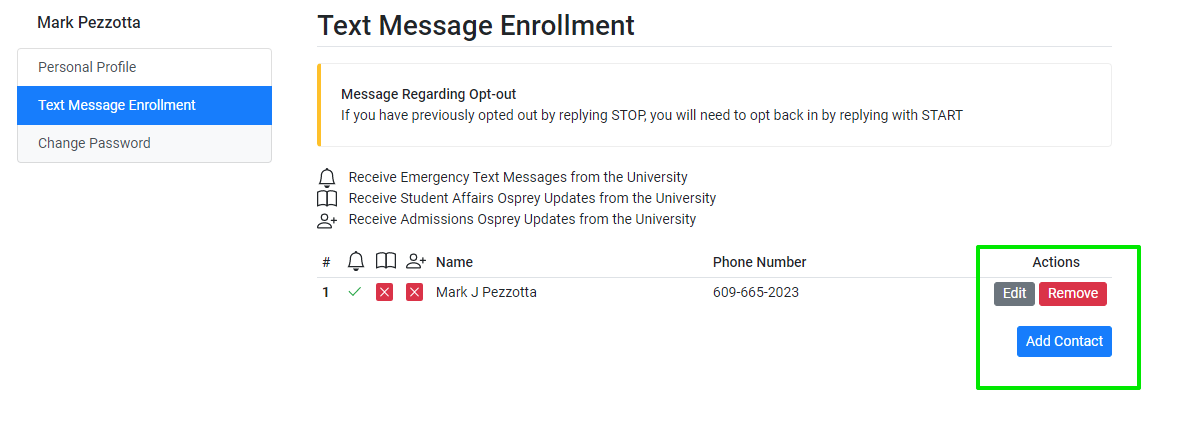
If you need to update your password or change the number on file for Stockton's Text Message Enrollment service, complete the following steps below. If you don't know your password, you can try resetting it using our self-service password reset form here: https://cas.stockton.edu/sspr/verify. If you need help with resetting your password, please contact the Stockton University ITS Help Desk: https://stockton.edu/information-technology/request-help.html. Please note that you will need to present a photo ID to verify your identity to receive a new temporary password.
How to Update Your Password or Text Message Enrollment Information

2.) Click on "Login to goStockton Portal"

3.) Click on "Update My Account"
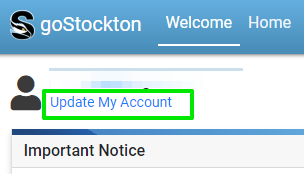
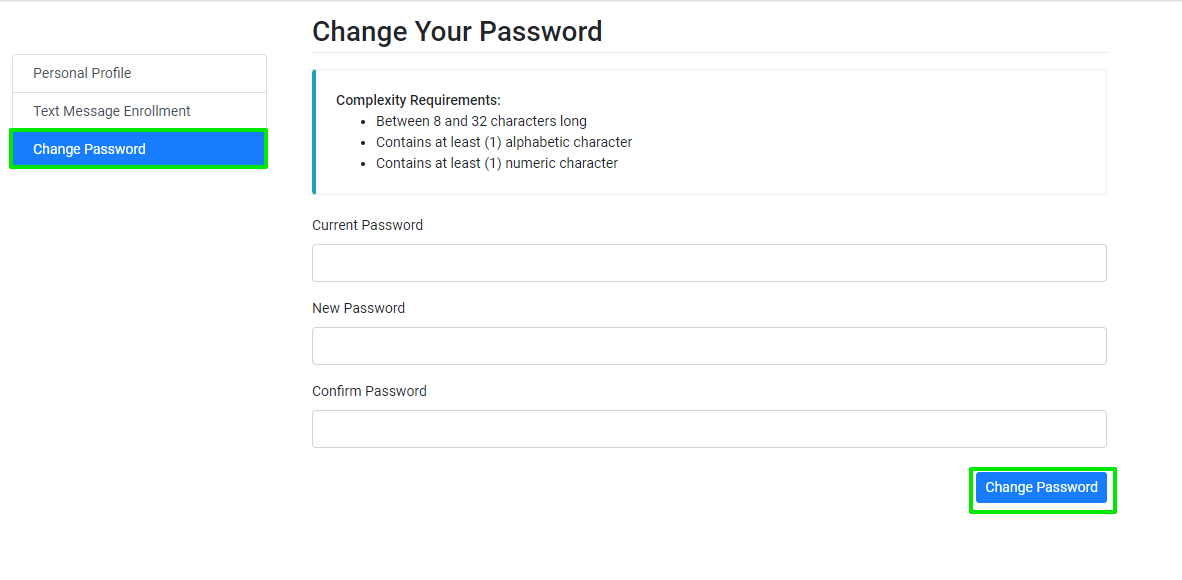
4.) Enter your information in the fields provided, meeting all of the complexity requirements.
From the Stockton home page (https://stockton.edu/), click on Go
- Enter your Stockton username & password and click on Login
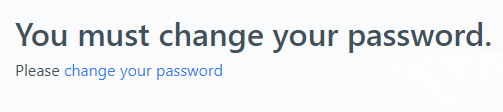
- If prompted, click on change your password
- Enter your current password and your new password twice. Make sure your new password
contains at least 12 characters and no more than 64 characters.
- Click on Submit. You’ll see the message below if your password has been successfully
reset

- Click on Home below to return to the Stockton home page (https://stockton.edu/)
- Click on Go and log in to the Stockton Portal with your username and your new password
- Click on Go and log in to the Stockton Portal with your username and your new password
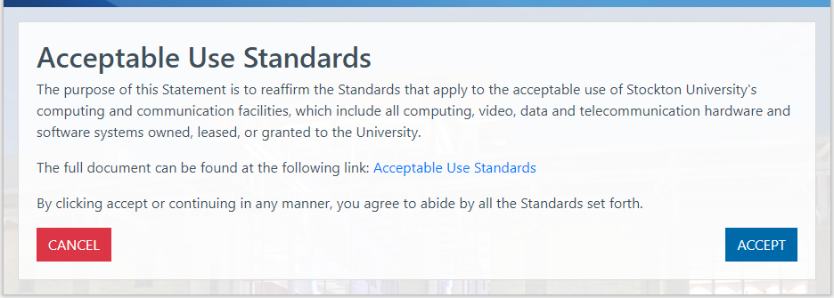
- The Portal will prompt you read the Acceptable Use Standards. If you agree to abide
by all the Standards set forth, click on Accept to continue
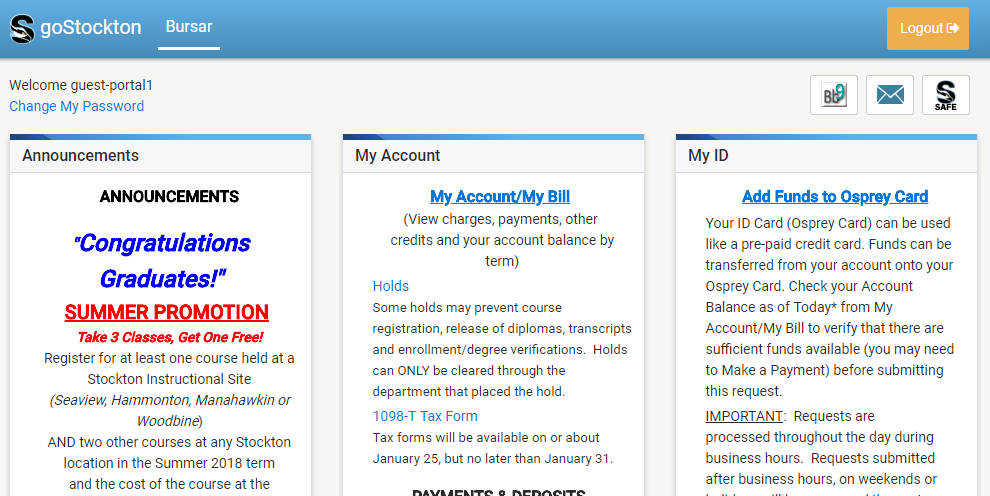
- Now you are ready to use the goStockton Portal and all the resources available to
students
Proxy Accounts (Academic Records)
Students may authorize a third party as an account proxy to view information associated with their Stockton University GoPortal account. Under the Family Educational Rights and Privacy Act (“FERPA”), students themselves retain the primary authority to grant or deny access to their academic records. Therefore, the student must initiate the proxy access process and fulfill each required step for the designated proxy to gain access to their account information.
Proxy access provides a designated person access to the students
- Unofficial transcript
- Tax forms (ex:1098-E)
- Account summary and charges by term
- Financial Aid Status
For more information on designating a proxy user, changing the level of access for a proxy user, or resetting a proxy PIN, please visit the Office of Student Rights FERPA and Proxy Access page.
Touchnet Authorized Users (Tuition Payments)
Stockton utilizes the Touchnet platform to process payments which are applied to students' account balance. If another person will be making payments toward your account balance, it is possible to give that person direct access to do so with an Authorized User account inside the Touchnet paymeny portal.
To add an authorized user, first access Touchnet. Navigate and log in to your GoStockton Portal, then under the Bursar tab, click on "Make a Deposit" or "Make a Payment".
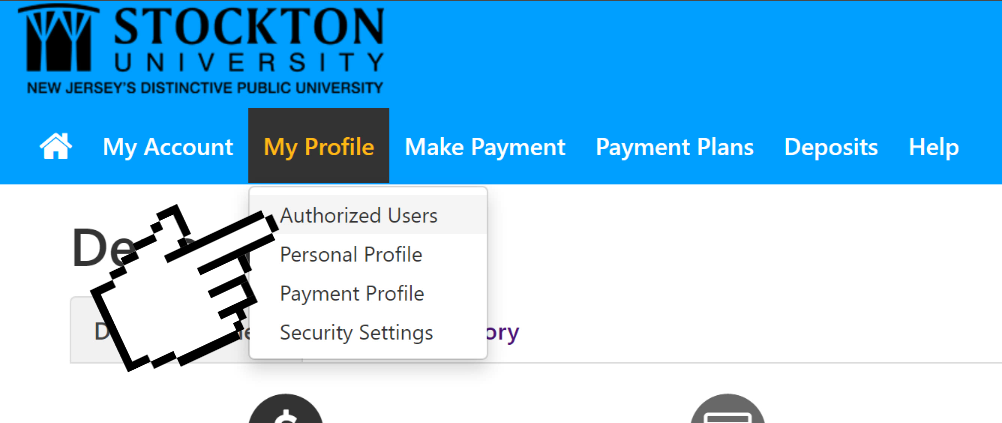
- Click on the My Profile button, then Authorized Users.
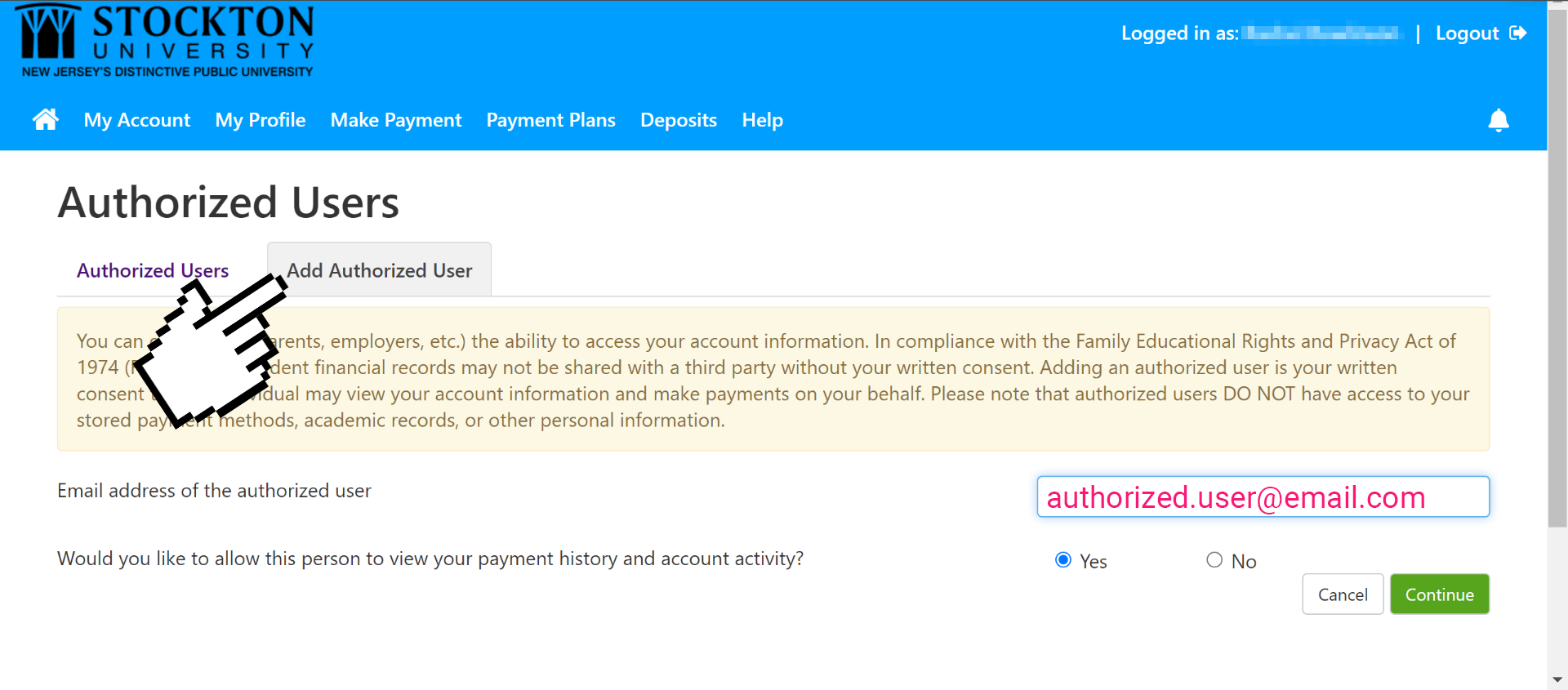
- Navigate to the Add Authorized User tab, then enter their email address.
- Complete the agreement and click continue, your new Authorized User will receive two emails: one with a link to log in to Touchnet, and one with a temporary password.
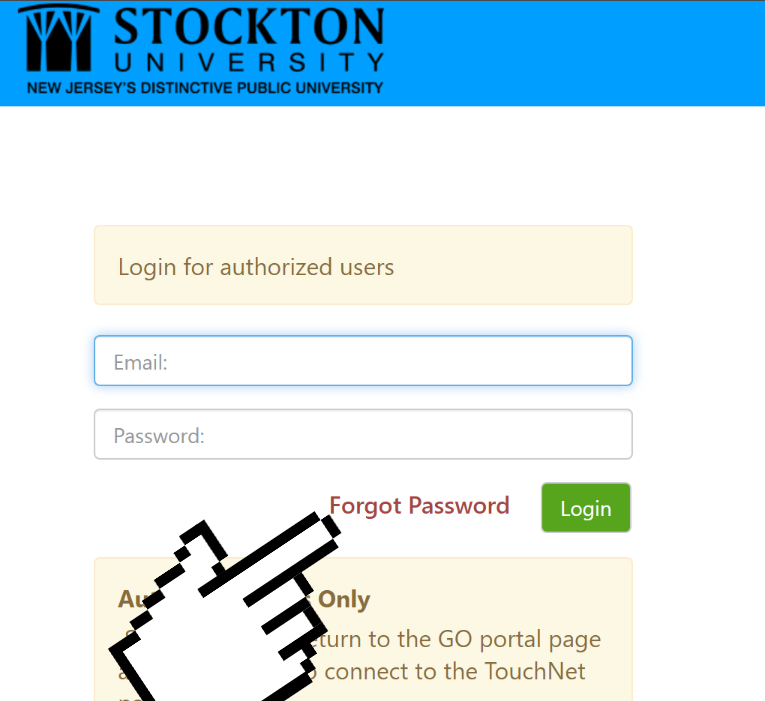
Authorized users may log in to Touchnet by following this link.
To reset their Touchnet password, authorized users should first access Touchnet. Click on the Forgot Password option and fill in their login email address.
The authorized user will receive a temporary password and will be prompted after login to set a new password.